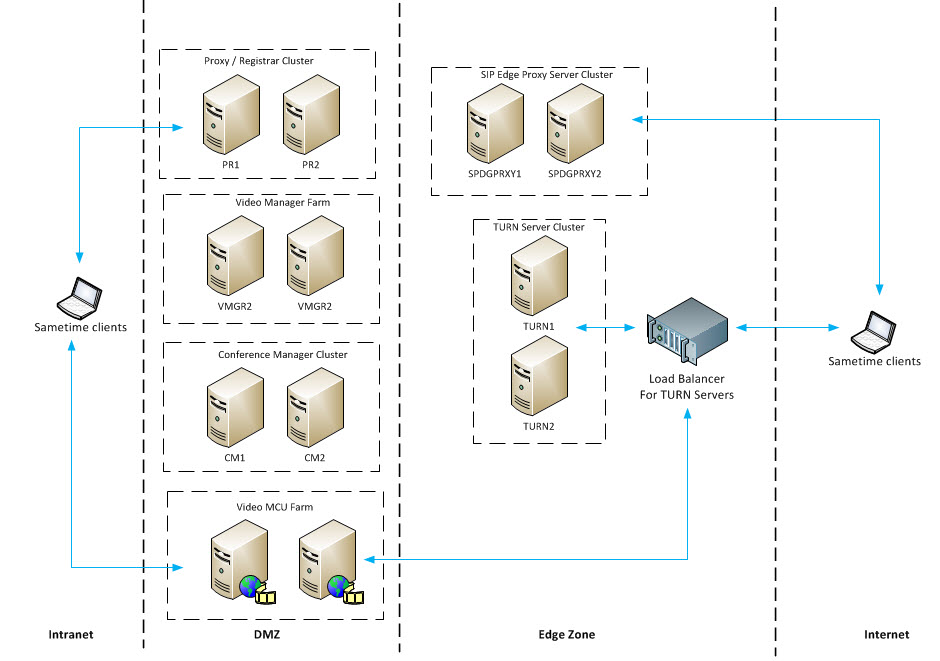
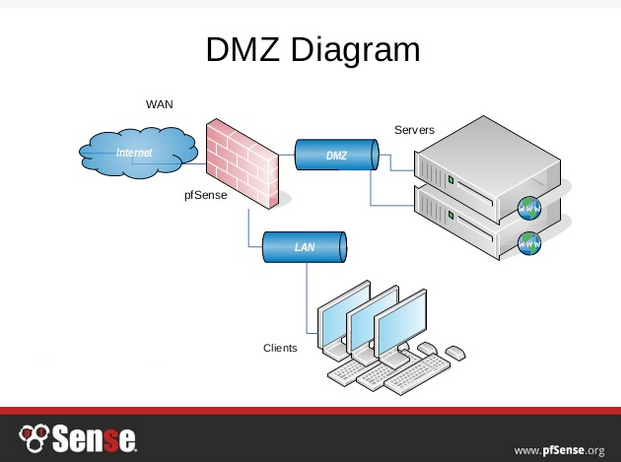
What is the best practice for placing database servers in secure network topologies - Information Security Stack Exchange
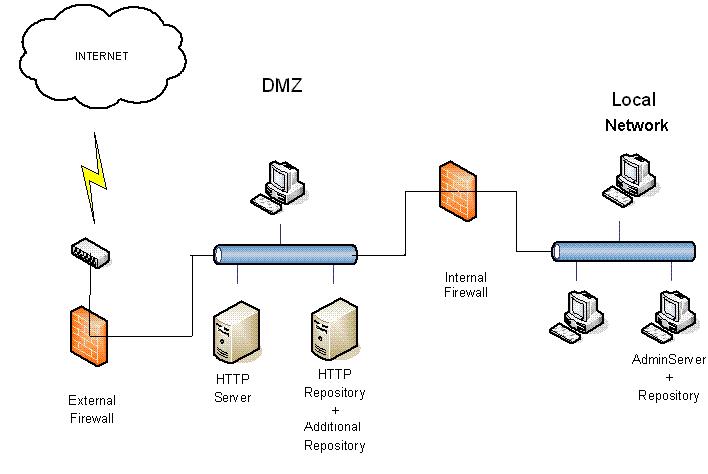
How to install Roaming when the HTTP server, the additional repository and the HTTP repository are in the DMZ? - Technical Support - Panda Security

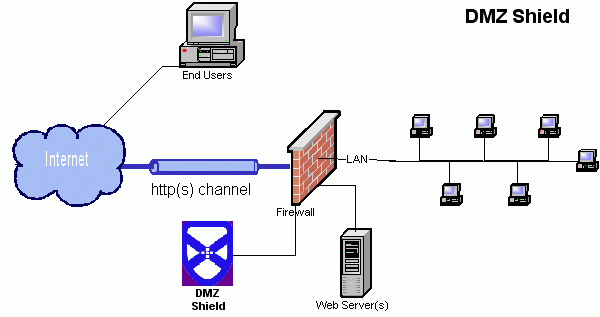
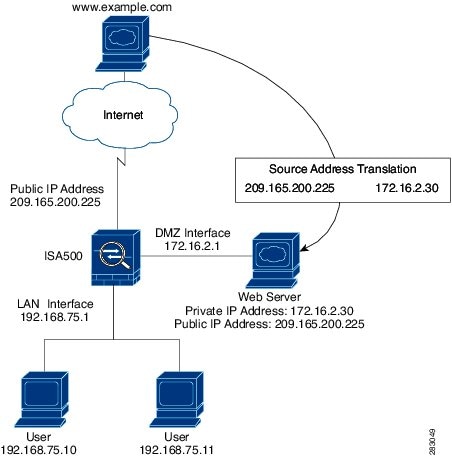
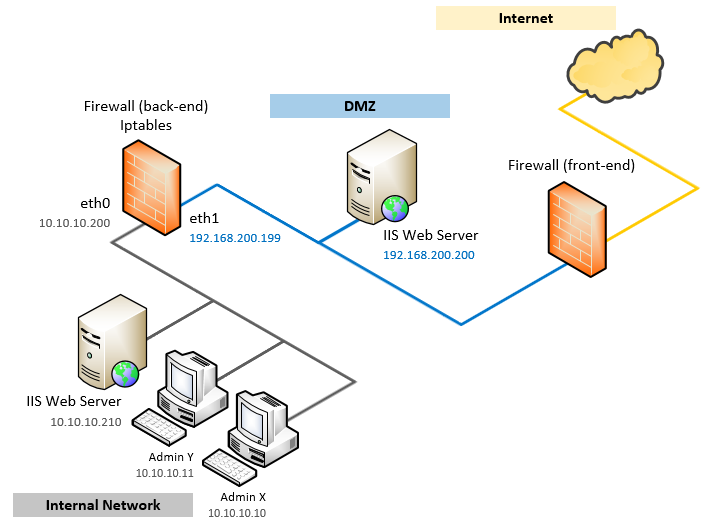
networking - Should I dual home our webservers (DMZ/Internal network) or just do 1-to-1 NAT? - Server Fault
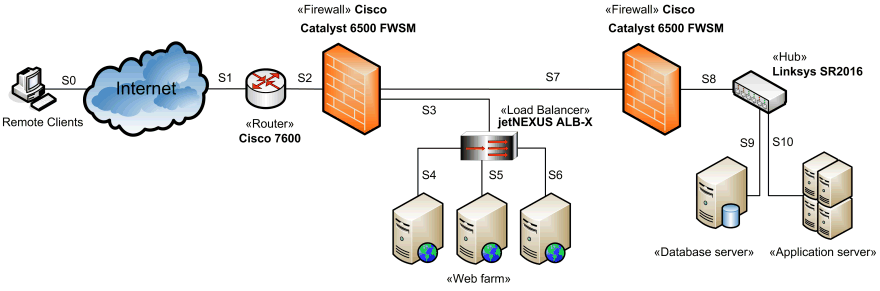
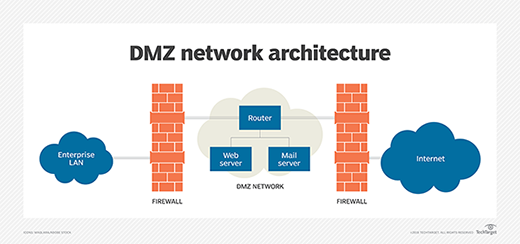
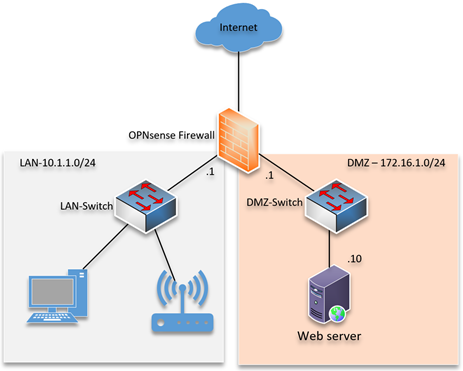
Web application network diagram example for online shopping with configuration called two firewall demilitarized zone (DMZ).